If you have a plugin called “Display Widgets” on your WordPress website, remove it immediately. The last three releases of the plugin have contained code that allows the author to publish any content on your site. It is a backdoor.
The authors of this plugin have been using the backdoor to publish spam content to sites running their plugin. During the past three months the plugin has been removed and readmitted to the WordPress.org plugin repository a total of four times. The plugin is used by approximately 200,000 WordPress websites, according to WordPress repository. (See below)
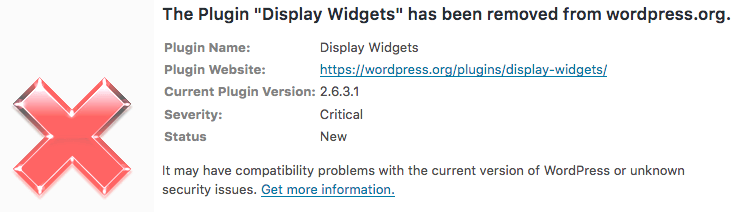
Wordfence warns you if you are using a plugin that has been removed from the repository. During the past months you would have been warned several times that this plugin has been removed with a ‘critical’ level warning that looks like this:
It turns out that this plugin did have “unknown security issues”. Let’s start with a timeline of what happened to Display Widgets, why it was removed three times from the repository and allowed back in each time and then finally removed again a fourth time a few days ago.
A Timeline of “Display Widgets” Bad Behavior
On June 21st a plugin called Display Widgets was sold by its owner to a user known as ‘displaywidget’ on the WordPress.org forums. That new owner released version 2.6.0 of the plugin.
On June 22nd, David Law, a UK based SEO consultant sent an email to the WordPress.org plugin team letting them know that the Display Widgets plugin was installing additional code from an external server. The plugin was downloading a large Maxmind IP geolocation database of around 38 megabytes from the author’s own server. This is not allowed for WordPress plugins in the repository.
On June 23rd, the plugin team removed Display Widgets from the repository. There was some discussion about this on the WordPress.org forums.
Then on June 30th, 7 days later, the developer released version 2.6.1 of the plugin. This release contained a file called geolocation.php which, no one realized at the time, contained malicious code.
The code in geolocation.php allowed the plugin author to post new content to any website running the plugin, to a URL of their choosing. They could also update content and remove content. Furthermore, the malicious code prevented any logged-in user from seeing the content. In other words, site owners would not see the malicious content.
David Law again contacted the plugin team and let them know that the plugin is logging visits to each website to an external server, which has privacy implications.
On July 1st the plugin was once again removed from the WordPress repository.
On July 6th version 2.6.2 of Display Widgets was released and it again included the malicious code referenced above which had still gone unnoticed by anyone. It included a change to the logging code which was disabled by default and included an on/off option. At the time David Law let the WordPress.org plugin team know that this was not enough in his opinion and they ended up disagreeing on the issue.
On July 23rd, Calvin Ngan opened a Trac ticket reporting that Display Widgets was injecting spammy content into his website. He included a link to Google results that had indexed the spam and said the malicious code is in geolocation.php.
On the 24th of July the WordPress.org plugin team removed Display Widgets from the plugin repository for a third time.
On the 2nd of September version 2.6.3 of the plugin was released and it included the same malicious code. Line 117 of geolocation.php in version 2.6.3 even contains a minor bug fix to the malicious code, which makes it clear that the authors themselves are maintaining the malicious code and understand its operation.
On September 7th a forum user on WordPress.org reports that spam has been injected into their website on the Display Widgets plugin support forum.
The author responds on September 8th saying:
“thank you for letting me know. Yes, the last update fixed this you need to clear your cache and update to the latest version. As I mentioned in the changelog, I asked a friend of mine to review the code and he gave me a full report. You can look at the wp_options table for leftovers, and if you don’t find anything then you should be okay.”
And then another reply from someone else sharing the same ‘displaywidget’ user account (spelling mistakes included):
—
Hi,
The other admin here. Unfortunately the addition of the GEO Location made the software vulnerable to a exploit if used in conjunction with other popular plugins.
The latest update fixed and sanitised the vulnerability. A simple empty of the cache & clearing of the wp_options table (if affected) should remove that post.
Again i apologise. But this should fix it. We estimate only around 100 or so sites to be comprimised.
Thanks
DW
—
The malicious code is not an exploit. It is a backdoor giving the author access to publish content on websites using the plugin. It does not require ‘other popular plugins’ to work.
The second poster says “only around 100 or so sites” are compromised. Actually, the backdoor exists on any site running versions 2.6.1 to version 2.6.3 of the plugin. Considering the time-span of 2.5 months between those releases, that would mean that these two or more people have access to publish anything they like on most of the 200,000 sites the plugin is installed on.
On September 8th the plugin was removed for a fourth time from the WordPress plugin repository. This time we hope it is permanent.
Wordfence Issued ‘Critical’ Alert Each Time Plugin Was Removed
On June 15th of this year, Wordfence added a feature to alert you if a plugin is removed from the repository. We did this because in the past, plugins have been removed because they have a security issue. It turns out that this feature helped users recognize that there was a security issue with this plugin.
We started alerting when this plugin was first removed, over two months ago:
We then continued to alert as the plugin was removed from the repository and re-added several times, as is the case in this forum post:
I’m incredibly proud that our team took the initiative and got this feature released in June of this year, just in time to save many of our free and paid customers from being affected by this malicious plugin.